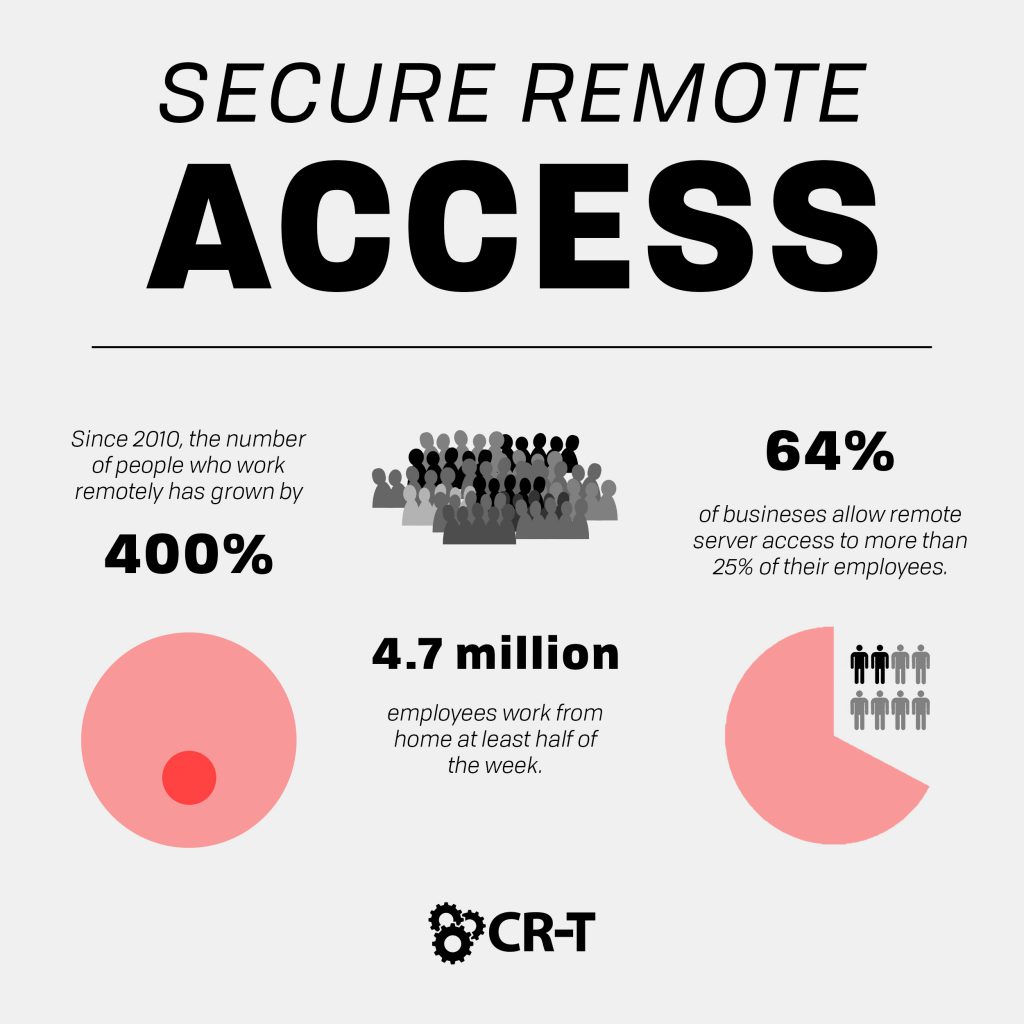
It’s no surprise why remote work is suddenly becoming so popular. Working remotely saves money by reducing travel and office expenses. And it’s often a lot more convenient for employees, especially those working across the globe. In the United States alone, 4.7 million employees work from home at least half of the week (Global Workplace Analytics). But accessing company data remotely also introduces greater risks, calling for new forms of security. In this article, we’ll discuss how secure remote access can benefit your organization and keep your data secure while working remotely.
What is Secure Remote Access?
Secure remote access refers to any security solution that prevents unauthorized access to a specific account or network.
Secure remote access makes it possible to create varying levels of authorization for different employees. An entry-level employee might only have access to a portion of the company’s data, while an executive will have much greater privileges when it comes to accessing secure data.
Additionally, secure remote access allows employees to safely manage data when working from a remote location. This is ideal for organizations who require a lot of traveling or who hire employees from around the globe.
Under the umbrella of secure remote access, there are a variety of specific measures you can take to secure your network. Let’s look at some of these a little more in-depth.
Virtual Private Network
A Virtual Private Network (VPN) establishes a secure Internet connection over an existing network. Through authentication and encryption methods, a user can access a public wifi network while still maintaining privacy.
VPNs are especially helpful because they make it impossible to track and use your data. This allows you to keep your search history and sensitive data private.
Multi-Factor Authentication
When it comes to securing sensitive information, Multi-Factor Authentication (MFA) is a great alternative to a standard password.
Instead of simply entering a series of characters, multi-factor authentication requires you to provide two or more forms of credentials in order to access certain information. This secures your data by offering additional protection in case a hacker discovers your password.
Another benefit of multi-factor authentication is its ease of use. Instead of trying to remember dozens of passwords, multi-factor authentication utilizes things you already have—like your phone or fingerprint—to authenticate your identity. This also makes it more difficult for someone to hack into your account if they lack the proper tools.
Desktop Sharing
Desktop sharing is a great option for a user who only needs temporary access to a specific device or an account.
For example, our service technicians at CR-T use desktop sharing to provide remote support to many of our clients. Through screen sharing, they can view another computer screen remotely and troubleshoot various solutions to technical problems. This saves them the time and cost of traveling to a client’s onsite location every time a problem occurs.
Desktop sharing can also be used to share files and data located on another computer. Remote login makes it possible for you to log into your work computer from home. It also allows for easier collaboration between coworkers.

Privileged Access Management
Finally, Privileged Access Management (PAM) allows you to create various levels of access management on different accounts. This will give privileged accounts access to sensitive data, while lower-level employees will be blocked from these accounts.
The same idea works when sharing information with vendors. Vendor Privileged Access Management gives vendors access to monitor and manage sensitive data through privileged credentials.
Least privilege is a good tactic if you want to limit employee access to company data. With least privilege, only a small handful of users have access to sensitive information, making it easier for you to manage control of these accounts and reduce the overall security risks.
Why Choose Secure Remote Access?
- Potential data loss
- Weaker passwords
- Increased risk of phishing attacks and ransomware
- Weaker antivirus and firewall protections
- Lack of computer inspections
How to Implement Secure Remote Access
Now that you understand secure remote access and its benefits, you can create and implement a security plan for your organization.
1. Develop a Cybersecurity Policy for Remote Workers.
The best way to prevent your data from falling into the wrong hands is through educating your employees. Employee error is one of the greatest risks to your organization, but your employees can become a valuable asset when they understand this risk.
If possible, only allow company-owned devices for remote work. This gives you the greatest control over what is stored on the device and which security features are used to protect the device’s data.
Create a service-level agreement for vendors, and educate both employees and vendors on the remote security policies you create.
2. Choose a Remote Access Solution.
Even after educating your employees, you can’t depend on them to have full control over your data’s security. Instead, choose a remote access solution (or multiple solutions) to provide added protection to your data.
The secure remote access solutions we discussed above are all great options, but it’s up to your company’s executives to decide which solution is right for your organization.
3. Implement Password Management and Multi-Factor Authentication.
Whether employees are accessing data onsite or remotely, it’s important to have strong passwords and security to protect vital information.
Password management software provides greater security than simply allowing each employee to choose a password. With password management, you have the power to generate random, complex passwords, require frequent password changes, and store passwords in a secure location.
Additionally, you should require multi-factor authentication before allowing access to sensitive data, especially if the employee is logging into a new device for the first time.
4. Create Employee Cybersecurity Training.
Finally, hold frequent trainings to educate your employees on best security practices. Encourage employees to lock their computers when not in use and to be aware of potential onlookers when working in public places.
Run phishing campaigns to train employees on social engineering attacks. Teach them how to recognize and respond to these attacks in order to minimize risk.
The more you prepare your employees, the less risk you face when allowing them to access secure information remotely.
Secure Remote Access: Your Path to Greater Freedom and Security
There are many obvious benefits to working remotely, and in the modern age of technology, more workers are taking advantage of this trend than ever before.
In order to protect sensitive data while working remotely, it’s important to have strict policies in place, including some form of secure remote access. Otherwise, you risk losing important data and jeopardizing your business.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.






