Many businesses struggle with security because they aren’t sure which factors create the most risk. When moving beyond antivirus and firewalls, security begins to feel complicated. BeyondTrust helps you move beyond the complexities to focus on a very important aspect of your business’s security: your employees. With BeyondTrust Privileged Access Management, you will limit the risk that employees and outside threats pose to the business.
BeyondTrust privileged access management solutions offer greater visibility and control, enabling you to reduce risk and achieve operational efficiency.
BeyondTrust Privileged Access & Session Management
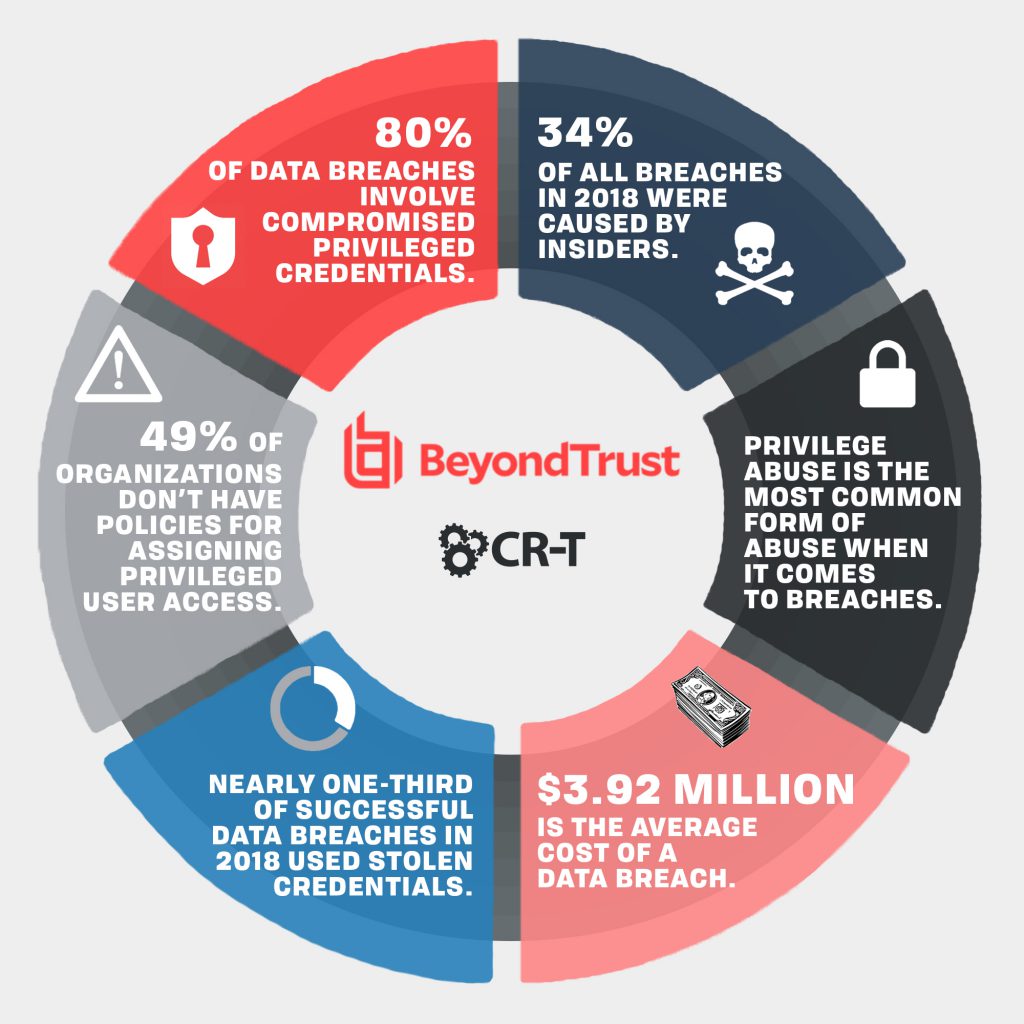
Did you know that 80% of security breaches are the result of privileged credential abuse or misuse (BeyondTrust)? BeyondTrust has the broadest set of credential management capabilities so that you can find a solution tailored to fit the needs of your business.
Password Safe
- Automated discovery
- Privileged session management
- App-to-app password management
- Secure SSH key management
- Adaptive access control
- Privileged threat analytics
Cloud Vault
Like Password Safe, Cloud Vault allows you to better manage privileged credentials. Cloud Vault acts as a single solution to managing sessions, passwords, vendor access, and more.
Discover and manage passwords for Windows platforms, then easily integrate the credentials on-demand with Cloud Vault. In addition to greater control and efficiency, Cloud Vault makes it easier to stay compliant. Keep track of user activity with a comprehensive audit report, including video recordings, logs, and session forensics.
Cloud Vault simplifies password management. Safely store login credentials—like usernames and passwords or SSH keys—for every privileged account in your organization. By consolidating the management of privileged accounts to one location, you are also lowering the risk of a cyber attack.
Credential injection allows administrators to access systems with a single click, helping you save time. Cloud Vault also provides end-to-end security for remote access sessions, regardless of your location.
DevOps Secrets Safe
Credentials and secrets are prime targets for attackers. Secure and manage sensitive information with DevOps Secrets Safe. DevOps provides a centralized administration solution that reduces risk without slowing down the application delivery process.
With DevOps Secrets Safe, you can automate your security across your development operations environment. Drive faster adoption and increased productivity as you integrate with common DevOps tools like Ansible, Jenkins, and Azure DevOps.
One of the key features of DevOps Secrets Safe is centralized administration. This gives you control over all secrets and privileged credentials, with the power to manage them from a single location.
Create an audit trail of all secret operations so you have full visibility over who accesses confidential information. Enjoy easy API interaction and enterprise-class performance when you switch to DevOps Secrets Safe.

BeyondTrust Endpoint Privilege Management
Over a third of businesses experience more than one serious security breach every year (Solutions Review). You can prevent attacks against your business by limiting privileges on Windows, Mac, Unix, Linux, and other networked devices.
Least privilege is the practice of restricting user access to only those accounts that are absolutely necessary. This makes it easier for you to manage access control and reduce security risks associated with storing sensitive information.
While least privilege is relatively easy to understand, it can often be difficult to implement, due to heterogeneous systems, an expanding number of endpoints, many different types of user roles, and other factors.
BeyondTrust can help you manage your endpoint security by implementing least privilege within your business. This will allow for greater security, without affecting the speed or efficiency of your workflow.
Windows and Mac
Stop malicious attacks by installing Least Privilege on your Windows and Mac devices. BeyondTrust offers a revolutionary approach to privilege management that secures your devices without impacting productivity.
Privilege Management elevates applications, not users. Utilizing least privilege on your Windows and Mac systems increases user productivity while eliminating 81% of vulnerabilities (BeyondTrust).
Application control protects your endpoints from infection by whitelisting approved applications and giving you total control over which programs users can install and run. Privileged threat analytics give you full visibility of user activity and allow you to analyze user behavior.
You can implement least privilege on day one. Default rules account for over 80% of use cases. Exception handling covers the remaining 20%.
With experience implementing privilege management across 50 million endpoints, BeyondTrust is the perfect choice to enhance your endpoint security.
Unix and Linux
Superuser accounts offer employees and clients virtually unlimited privileges. These accounts may even give the user power to make systemic changes across a network, including installing new files and software, modifying settings, and deleting users and data.
In Linux and Unix systems, superuser accounts give the user access to all commands, files, directories, and resources. This creates a potential for abuse and can be remedied by only assigning superuser accounts to admins.
In contrast, standard accounts retain minimal default privileges, allowing you to customize privileges as needed. Unix and Linux systems are high-value targets, making it more important than ever for you to minimize privileged accounts.
BeyondTrust Privileged Management allows you to create privilege elevation roles for users, audit user activity, and monitor suspicious users. This architecture allows for centralized policy management and auditing, providing you with greater security and control.
Active Directory Bridge
Active Directory (AD) Bridge extends Microsoft’s Active Directory capabilities to Unix, Linux, and Mac systems. AD Bridge increases efficiency, streamlines compliance, and enhances security.
BeyondTrust AD Bridge integrates Unix, Linux, and Mac into a Windows environment. This allows users to leverage their AD credentials with multiple systems and transition between systems without having to re-enter credentials.
AD Bridge also streamlines the management of complex environments. Users can audit multiple events in real time and simplify management by consolidating directories. Additionally, configuration remains consistent across multiple platforms.
BeyondTrust AD Bridge can help you achieve the following:
- Centralized configuration
- Lower costs
- Simplified user management
- Easier compliance
- Enhanced security

BeyondTrust Secure Remote Access
Remote support will empower your services team to support Windows, Mac, Linux, iOS, Android, and other network devices with a single tool. Additionally, vendors will be able to centrally manage and secure remote access.
Remote Support
BeyondTrust Secure Remote Access enables you to support more devices, platforms, people, and locations. Provide more reliable support to customers, both on and off the network. High-quality remote support means exceptional service and higher customer satisfaction.
A top tier remote support solution also means greater security. Support teams need administrative access to critical systems in order to do their jobs effectively. A secure remote access tool ensures that your network will stay protected from threats while meeting compliance regulations.
Privileged Remote Access
In addition to support teams, BeyondTrust provides privileged remote access for insiders and vendors. While standard access is sufficient for most users, admins and high-level users need access to critical assets, while still maintaining security.
BeyondTrust Privileged Remote Access makes it possible for contractors and vendors to access necessary information without a VPN. Privileged Remote Access provides a system that allows users to do their jobs more quickly and easily than ever before.
BeyondInsight: Your Ally Against Cybersecurity Threats
BeyondInsight is the tech industry’s most innovative and comprehensive privileged access management platform. BeyondInsight makes it easier to:
- Maximize visibility
- Simplify deployment
- Automate tasks
- Improve security
- Reduce privilege-related risks
With BeyondInsight, you more easily correlate vulnerability information with user activity and learn how to reduce security risks across complex environments.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of





