Securing customer data is essential for one major reason: your business depends on it.
As an IT director, you recognize the importance of cybersecurity when it comes to your organization’s processes and workflows.
And for those who have suffered a data breach, you know how important it is to prioritize strong security measures and policies.
Whether you already have substantial security in place or you’re just getting started, here are 6 steps you can take right now to secure customer data.
Step 1. Keep Only the Data You Need.
By only collecting the data that’s vital to your business, you accomplish two things:
- You decrease the external value of your data.
- You increase your clients’ confidence.
The greater the number of data points that your organization collects, the more valuable this data is to outsiders.
By limiting the amount of data you collect, the less likely a hacker is to try and steal the information from you. For example, if all a hacker can gain from you is an email address, they might not put forth the effort.
Only collecting vital data will increase client confidence as well.
If your organization is collecting data that doesn’t seem relevant or necessary to your business practices, then a client might begin to question your intentions.
Being transparent about how and why you collect data will build greater trust among your clients.
Audit Your Organization’s Data Collection
To evaluate which data is vital to your organization, periodically audit every piece of data you collect.
Ask yourself the following questions:
- What are the consequences of collecting this data point?
- What are the consequences of not collecting this data point?
- If we didn’t collect this data point, would it drastically change the way we operate?
Regularly auditing your data collection will build trust among your clients and will ensure your organization remains compliant with data privacy laws.
Dispose of Unnecessary Data
Once you’ve determined which data is essential to your business, consider purging any data that doesn’t relate directly to your organization’s needs.
It can be helpful to create a privacy plan for your organization that dictates how long customer data will be stored, what format the data will be stored in, and how/when the data will be destroyed.
When destroying physical data, make sure to wipe computer hard drives and shred any documents before disposing of them.
Step 2. Limit Access to Customer Data.
One of the most effective ways to secure customer data is by limiting who can access that data.
Encrypt Customer Data
Encrypt sensitive data, along with any tools you might be using to retrieve or share that data—such as your email.
Hard copies of customer data should also be locked up. Adding additional measures like a numeric keypad or biometric verification can significantly increase your data security.
Network Access Control
Members of your organization should only have access to the data they need to perform their jobs.
Network Access Control (NAC) enables you to limit who can access your organization’s network. You can also create different levels of access based on an employee’s duties and the data they need to access.
Limiting access to customer data ensures there are fewer points of vulnerability for your organization.
Multi-Factor Authentication
In addition to NAC, every device and account within your organization should enable Multi-Factor Authentication (MFA).
Since MFA requires two or more forms of verification, a hacker is much less likely to be able to access your account, keeping your customer data more secure.
Step 3. Make Sure Your Security Measures are Up to Date.
Controlling who can access customer data is only one facet of your organization’s cybersecurity.
Ensuring your security measures are up to date is essential when it comes to securing customer data.
Install and Update the Right Security Software
When’s the last time you updated your antivirus software?
Security software is your first line of defense, but it won’t offer much protection unless you update it regularly.
Hackers are constantly finding new ways to exploit security vulnerabilities, and neglecting to patch and update your software leaves the backdoor open to these attacks.
Implement Backup and Disaster Recovery
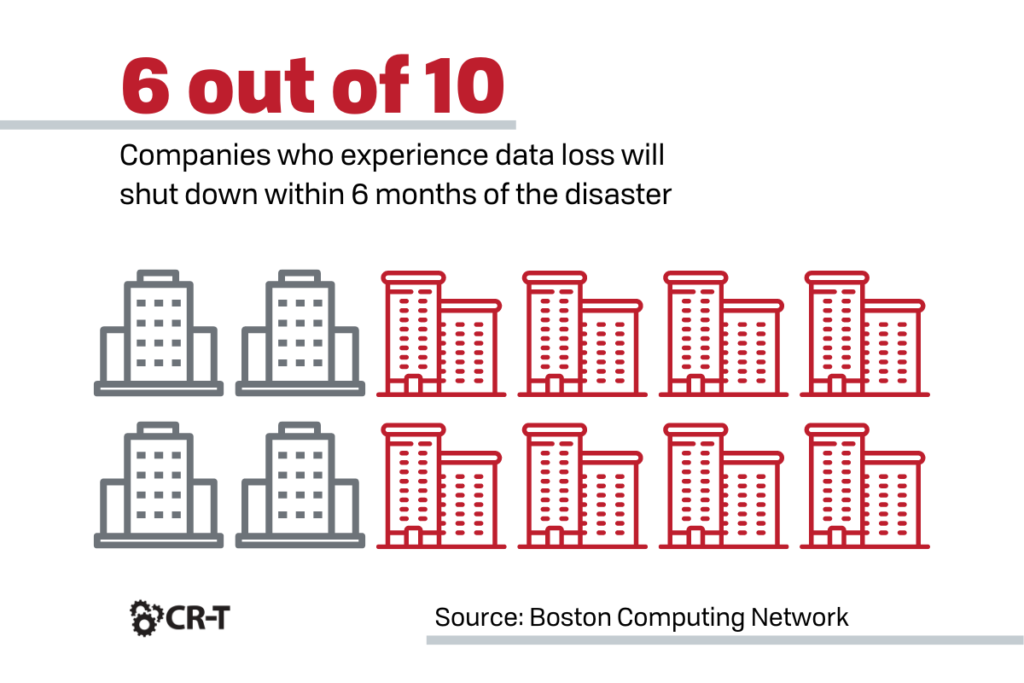
You can never eliminate the risks of data loss, but you can prepare to address these risks by implementing a Backup and Disaster Recovery (BDR) solution.
BDR acts as a safeguard against data loss and ensures that in the event of a cyber attack, day-to-day business functions can continue with as little disruption as possible.
Make sure that your BDR solution includes contingencies for a cyber attack, and include provisions for communicating with customers and employees.
Test for Vulnerabilities
Are you familiar with your organization’s vulnerabilities? Do you know where the gaps are in your cybersecurity?
Regularly testing for vulnerabilities will help you gain visibility into the strengths and weaknesses of your network security.
And learning about these weaknesses early will give you the time you need to make changes before a real attack hits.
Consider bringing in a cybersecurity expert to evaluate your system and provide recommendations for ways you can bolster your security.
Step 4. Develop an Incident Response Plan.
Having an incident response plan in place is just as important as any other preventative measure.
An Incident Response Plan will keep every member of your organization on the same page when it comes to security. A detailed plan will also help you recover from a data breach more quickly so you can avoid similar occurrences in the future.
What to Include in Your Incident Response Plan
If you don’t already have an incident response plan in place, work on creating one with your team. Here are some elements your plan should include:
- A detailed explanation of your organization’s incident response strategy and how it supports your business’s goals and objectives
- Procedures for each phase of the incident response process
- A list of roles and responsibilities relating to your organization’s security
- Communication procedures within the incident response team, the organization, and external stakeholders
- Questions that will help you learn from previous incidents to improve your organization’s security posture
Putting Your Plan into Action
Following a cyber attack, document every detail surrounding the breach.
- When and how was the breach detected?
- Which data/systems were affected?
- How was the breach contained and eradicated?
- Were any changes made to the systems/data during recovery?
- How was the response plan effective?
- How can the response plan be improved?
Contact any parties affected by the breach and investigate further if necessary.
You should also review your incident response plan regularly to ensure your policies and procedures are up to date.
Step 5. Train Employees in Security Best Practices.
Every member of your organization is responsible for understanding and prioritizing security.
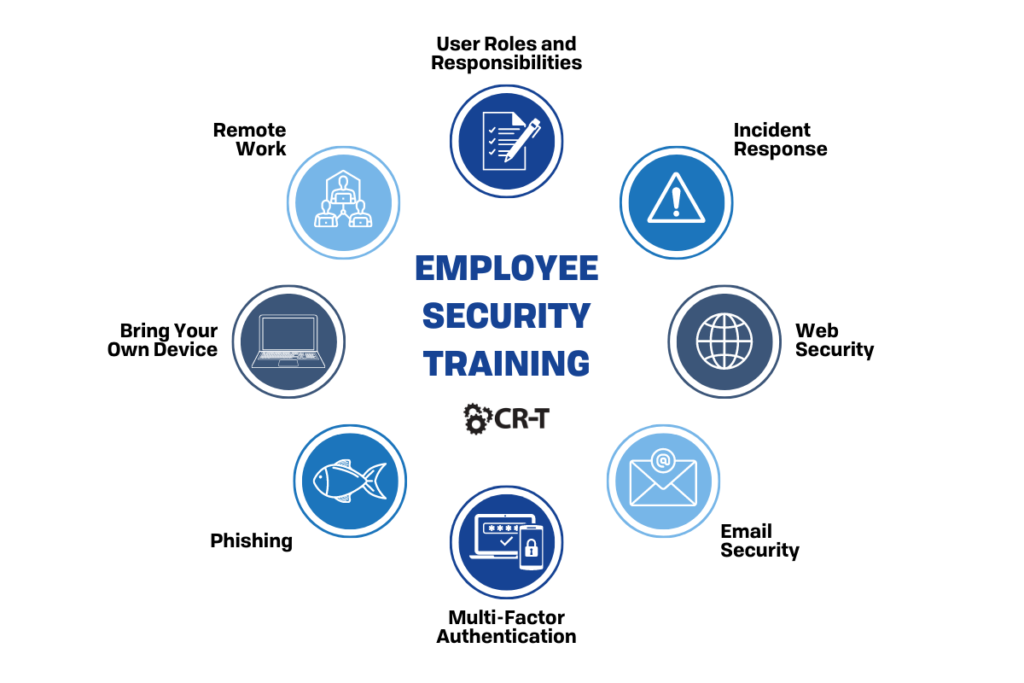
Train your employees in security best practices and ensure that every employee understands your organization’s security policies.
Here are a few of the most important security-related topics that employees should be familiar with:
- User Roles and Responsibilities
- Incident Response
- Web Security
- Email Security
- Password Management and Multi-Factor Authentication (MFA)
- Social Engineering and Phishing
- Bring Your Own Device (BYOD)
- Remote Work
Step 6. Be Transparent.
Finally, make sure your customers know exactly how their data is collected, stored, used, and protected.
Trust plays an important role in a customer’s willingness to share their data with your organization.
And with ever-changing compliance and data privacy laws, it’s more important than ever to ensure that your organization’s processes align with applicable laws, regulations, and policies.
Create a Privacy Policy for Your Organization
A privacy policy specifies how your organization collects, handles, and processes customer data.
Creating a privacy policy will help your customers better understand the reason for collecting their personal information, as well as how that data is being used.
A privacy policy will also ensure that every member of your organization understands the policies and processes surrounding data collection and storage.
Here are a few of the questions you should answer in your privacy policy:
- Which types of personal data does your organization collect and how is the information collected?
- How is the data being stored and used?
- Do you share customer data with third parties, and if so, how is the information shared and used?
- What steps do you take to secure customer data?
- What rights do users have when it comes to amending or removing their personal data?
- Does your website use cookies? If so, which information is collected, and how is it used?
- How will you notify users if you make changes to your privacy policy?
- Who can customers contact if they have questions about your organization’s privacy policy?
Conclusion
Regardless of your industry, securing customer data should be one of your top priorities.
Following the steps above will help you bolster your organization’s security and build trust with your clients.
In a world where data is passed around like candy, prioritizing data security will strengthen your company’s reputation and protect you against future attacks.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of

