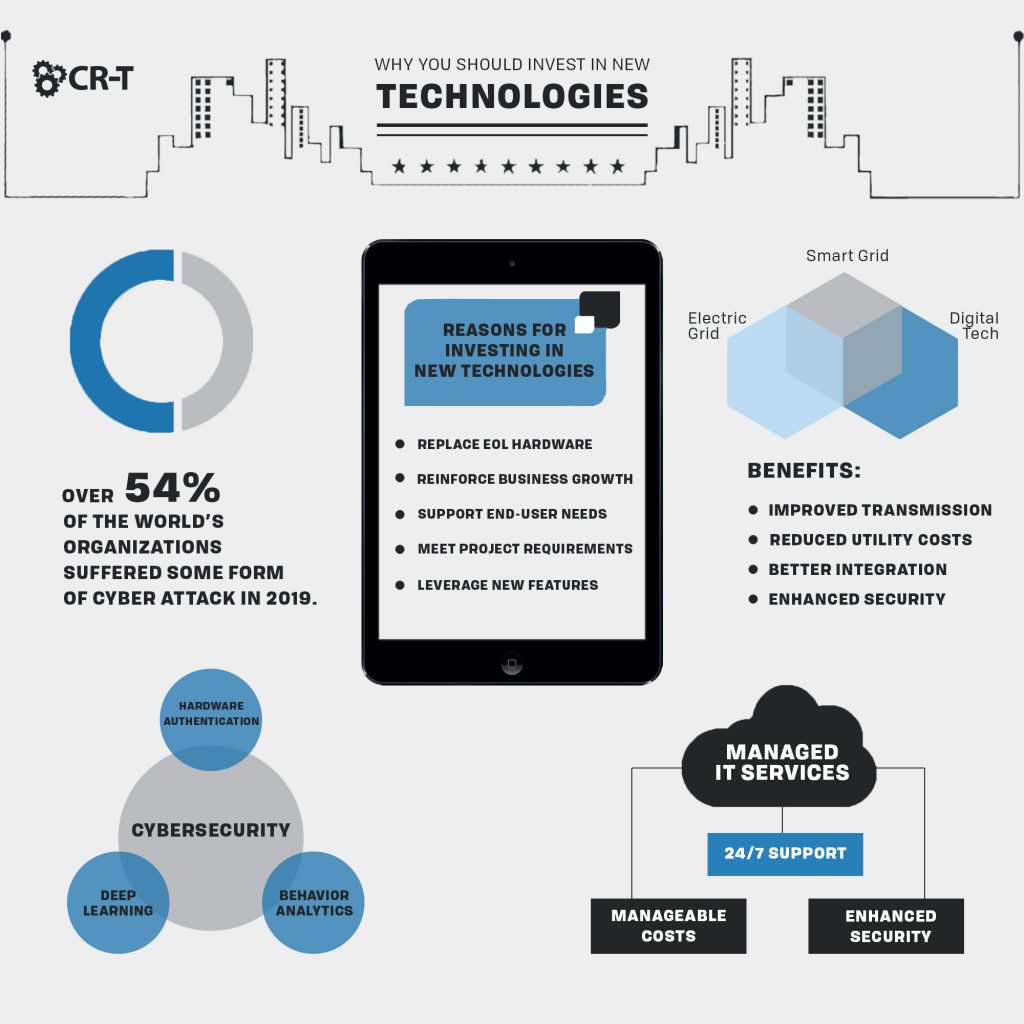
- To replace end-of-life (EOL) hardware
- To refresh cycles
- To reinforce business growth
- To support end-user needs
- To meet project requirements
- To leverage new tech features
- To improve software compatibility
Managed IT Services
As technology grows and IT becomes riddled with more tasks, small businesses will begin to look for help outside their organizations. Managed Service Providers (MSPs) offer support from experienced professionals at a fraction of the cost of hiring an in-house team.
Manageable Costs
Partnering with a MSP can save a lot of money in the long run. For one, you avoid the stress of having to manage your own team—and pay their salaries.
In addition, MSPs allow you greater flexibility and scalability than an in-house team. For small businesses, especially, it can get expensive to hire a full-time technician to fulfill all of your needs. Instead, an MSP offers you a team of experienced professionals at a monthly rate.
MSPs can also help you get deals on new products, and they can personalize their recommendations to fit your needs. You’ll have access to a variety of services, right at your fingertips—and at a much lower cost than you could find anywhere else.
24/7 Monitoring and Support
In addition to saving money, MSPs offer around-the-clock monitoring. That way, your technology is always protected.
Do you live in a different timezone from your managed service provider? No problem! MSPs also offer 24/7 support, so you can call in anytime you have a problem to get the help you need.
Enhance Security and Compliance
Cybersecurity is an ongoing endeavor, and it can be difficult to keep up with all of the latest information and trends. Managed IT services offers a professional look into how your business manages its cybersecurity.
An MSP can perform a comprehensive audit of your cybersecurity and bring vulnerabilities to your attention. Not only will managed services help you fill in the gaps. We will also help you prioritize your security needs so you can protect your most important assets first.

Cybersecurity
Over 54% of the world’s organizations suffered some form of cyber attack in 2019 (PhoenixNAP). And the number of cyber attacks isn’t going down. It’s going up.
Businesses can no longer afford to rely on outdated technologies for protection. Everyone is at risk of a security breach, but you can lower that risk by investing in technologies and best practices.
Behavior Analytics
Behavior analytics is advancing in its ability to monitor and detect suspicious activity. This is especially important for accounts with sensitive information, because it notifies businesses of unusual or malicious activity.
Once an attacker gains entry to a network, they can create all sorts of problems before the business even knows anything is wrong. With behavior analytics, these attacks can be detected and dealt with a lot sooner.
More advanced forms of behavior analytics go beyond simply differentiating malicious network activity. For example, bioprinting analyzes the way a user types or moves their mouse. Phone printing allows companies to analyze acoustic information in order to better identify spoof calls.
Smart Grid Technologies
- Improved transmission of electricity
- Reduced utility costs
- Better integration of power-generation systems
- Enhanced security
Hardware Authentication
Hardware authentication is an emerging technology that utilizes a physical device—in addition to a password—to authorize access to computer resources.
The device generates a unique, temporary cryptographic code that the user must input in order to gain access. Multi-factor authentication enhances security when it comes to accessing secure information.
In addition to hardware-based authentication, software-based apps provide a similar function, sending you a temporary code or push notification. These forms of authentication are revolutionizing the world of cybersecurity, making it both easier and safer for employees to log into their accounts.
Deep Learning
Deep learning combines various technologies, like machine learning and artificial intelligence (AI). Like behavior analytics, deep learning focuses on detecting and analyzing unusual behavior. But instead of tracking individual users, the technology focuses on “entities” as a whole.
Deep learning tracks behavior through artificial neural networks. These networks imitate the human brain and its functions in order to create patterns of decision-making. Deep learning gathers data from social media, search engines, and other platforms to improve its understanding of human behavior.
One of the biggest advantages of deep learning is its ability to independently execute feature engineering. After scanning large amounts of data, the algorithm combines similar features in order to operate faster and more effectively.

Protect Yourself From Growing Threats
While new technologies have certainly improved the state of cybersecurity, there are also many threats that have grown more harmful as technology evolves.
Deepfake Technology
Deepfake technology allows people to manipulate videos and audio in a way that appears very realistic. Just search the word “deepfake” on YouTube, and you’ll find dozens of videos where a famous actor or politician has been superimposed onto another person’s body. Even face swapping filters on Snapchat or Instagram employ a rudimentary version of deepfaking.
The problem is that with deepfakes becoming more sophisticated over time, cybersecurity experts worry that hackers could use the technology for phishing scams. It’s important to recognize the possibility of these threats so that you can protect yourself and your employees from falling prey to these schemes.
Quantum Computing
In addition to deepfake, quantum computing is making strides in the technology world. Just last September, Google announced that it had achieved “quantum supremacy.” While this is a major milestone, it also means bad news in the field of cybersecurity.
Quantum computers transform abnormal data from quantum physics into computing power. Some experts worry that this form of computing could easily break encryption, leaving secure information vulnerable.
While quantum computers are still an emerging technology, businesses should be aware of their potential to threaten encryption in coming years.
Internet of Things
Finally, the Internet of Things (IoT) introduces an increasing number of vulnerabilities, making it easier for hackers to compromise business operations.
IoT security has never been more important for businesses. With so many endpoints in a network, it’s essential for businesses to have strong security policies.
It will also become more important for developers to prioritize security at the design phase of any device or product. As technology continues to expand and evolve, businesses will need to create new strategies to combat these threats.
Why You Should Invest in New Technologies
Many businesses believe their current technology is strong enough to combat cyber attacks. Yet more businesses are experiencing security breaches than ever before. As of right now, 1 in 13 web requests leads to malware (Varonis).
Investing in new technologies isn’t simply about gaining a competitive edge. In the modern world, powerful technology is critical to maintaining your security. With new technologies, you can protect yourself from outside threats, while subsequently investing in the future of your business.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of





