You’re probably familiar with what it means to suffer a cyber attack. And you might feel confident in your ability to prevent an attack against your organization. But how well do you understand the anatomy of a cyber attack? Do you know what tools attackers use to target organizations, infiltrate their networks, and later cover their tracks?
In this article, we’ll delve into what goes on behind the scenes in a cyber attack. We’ll also offer tips on ways to prevent and respond to malicious intruders.
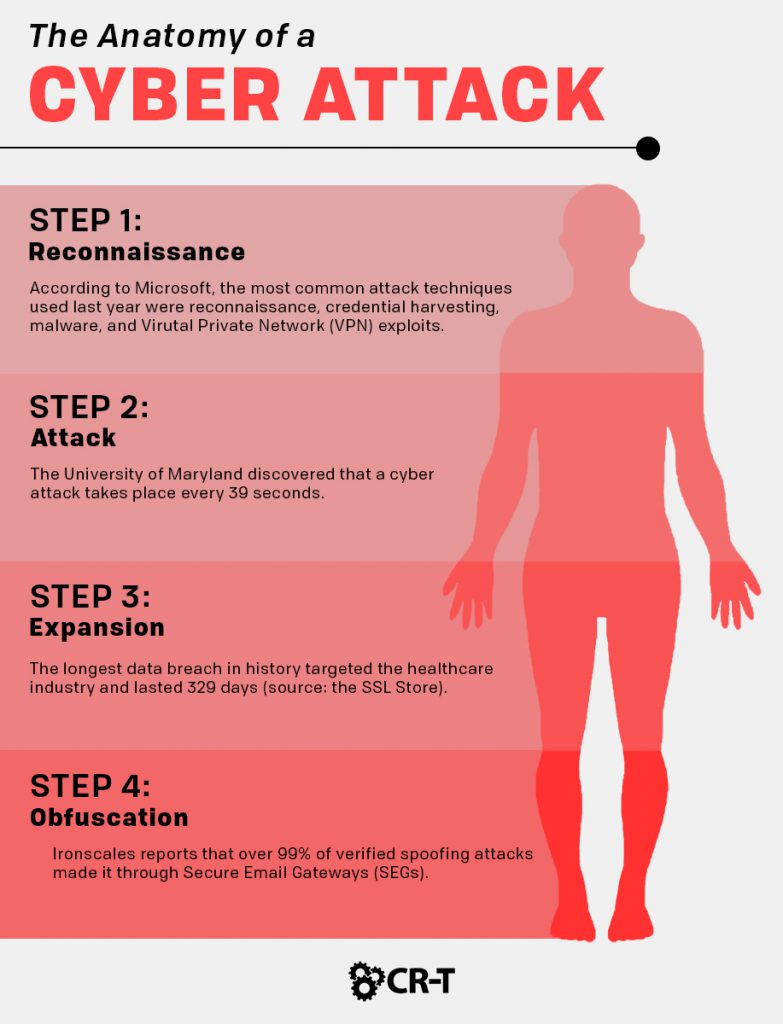
Step 1: Reconnaissance
When it comes to the anatomy of a cyber attack, the first step is usually reconnaissance.
Attackers will often research a target organization and gather as much information as possible. This includes network information, IP addresses, domain names, and the personal information of employees within the company, like the CFO and members of the IT team.
Next, attackers search for vulnerabilities in the network that will allow them to gain entry. This process often takes months of planning and involves a lot of trial and error.
Once the hackers are able to gain access to the network, they can begin the attack.
Step 2: Attack
Every cyber attack will look different, depending on the circumstances and type of attack.
After entering the network, hackers will often use a rainbow table or other tools in order to steal credentials from higher-level employees. This grants them administrator privileges and allows them to easily access the entire network.
At this point, attackers will generally try to steal sensitive information in order to encrypt it or sell it on the Internet. They may also infect the organization’s network with a virus or inflict other damage for financial gain.
Step 3: Expansion
After the initial attack, hackers will often utilize malicious programs to maintain their control of the network.
They might expand to multiple systems within the organization or utilize programs to maintain control of the network, even after being detected.
At this stage within the anatomy of a cyber attack, hackers can often continue to infiltrate the network without administrator privileges.
Step 4: Obfuscation
- Spoofing
- Log cleaning
- Zombied accounts
- Trojan commands
Cyber Attack Prevention
Now that you understand the anatomy of a cyber attack, what can you do to prevent one from happening?
Understanding the Motive
One of the first steps is understanding the motive behind these kinds of attacks.
The most common motive for conducting a cyber attack is financial gain. Hackers will often encrypt or steal data in exchange for a ransom. Sometimes, they even try to sell the data online.
Other motives include damaging an organization’s reputation, spreading fear through cyber terrorism, and distracting the authorities from other, more dangerous attacks.
Protecting Your Organization
Having a skilled team of cybersecurity experts is critical in order to prevent a cyber attack. They’ve spent years researching and studying the anatomy of a cyber attack, and they can help you develop a plan to prevent a cyber attack and minimize its effects.
To help protect your business, your cybersecurity efforts should include:
- Regularly testing your systems and network for vulnerabilities
- Installing firewall and antivirus software to protect your network from malware and other viruses
- Adopting multi-factor authentication for all employee accounts
- Implementing intrusion prevention technology that can detect reconnaissance attempts
- Encrypting your organization’s data
- Setting up alerts for outgoing data
- Conducting regular hardware and software audits to monitor the strength of your IT systems
- Training employees to educate them on how to prevent and respond to cyber attacks
Responding to a Cyber Attack
- Trace the attack to determine which device was initially infected.
- Establish how much information was compromised during the breach.
- Contact any customers whose information may have been affected.
- Perform a total security update to ensure that no other devices are infected.
- Update your security policies to prevent a similar attack from taking place in the future.
Applying Modern Technologies for Better Cybersecurity
Cyber attacks are evolving every year, making them more difficult to prevent and overcome.
However, technology is also improving, making it easier for businesses to withstand these attacks.
Through Artificial Intelligence (AI) and Machine Learning, cybersecurity experts are able to analyze the anatomy of a cyber attack and predict common attack strategies. These technologies are also making it easier for businesses to automate threat detection and data recovery.
And AI isn’t the only field making strides. Blockchain technology can help organizations detect data breaches by tracking any changes made to the blockchain. Blockchain also makes it easier to distribute data across a network, thus simplifying the process of data recovery.
Understanding the Anatomy of a Cyber Attack Will Help You Provide Greater Protection for Your Organization.
It’s impossible to prevent every cyber attack that might come your way, but understanding hackers and their motives can better prepare you to respond to these attacks.
By examining the anatomy of a cyber attack, you can learn the most common entry points and secure them against attacks. You’ll also be more prepared to identify data breaches early, thus providing greater protection to your organization.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of





