Anyone can prioritize network security.
Many of you have already done this with ease, establishing a strong foundation for your company’s cybersecurity.
But strong security isn’t just for large enterprises.
At CR-T, we started out with only a handful of employees over 20 years ago.
Now, we help dozens of companies manage their network security.
You can easily strengthen your own organization’s security by following the blueprint outlined in this guide.
Your 2-Minute Quick Start Cheat Sheet
In this section, we’ll go over the most essential steps to start you on the road to success.
First, create an inventory of your organization’s assets. This includes anything attackers might want to take control of, like devices, servers, and data.
Next, perform a risk assessment to identify potential threats and determine their impact on your organization.
Congratulations! You’re on your way to strengthening your organization’s network security.
But don’t celebrate too hard just yet—we’re not quite finished. From there, you need to develop a security strategy that addresses each of the threats putting your network at risk.
Let’s go through the whole process in detail.
- Perform Auditing and Mapping.
- Conduct Regular Risk Assessments.
- Keep Your Network Up to Date.
- Understand Network Traffic Patterns.
- Understand User Behavior.
- Implement a Backup and Disaster Recovery (BDR) Solution.
- Establish Strong Authentication Controls.
- Develop an Incident Response Plan.
- Train Your Users.
- Invest in Cyber Insurance.
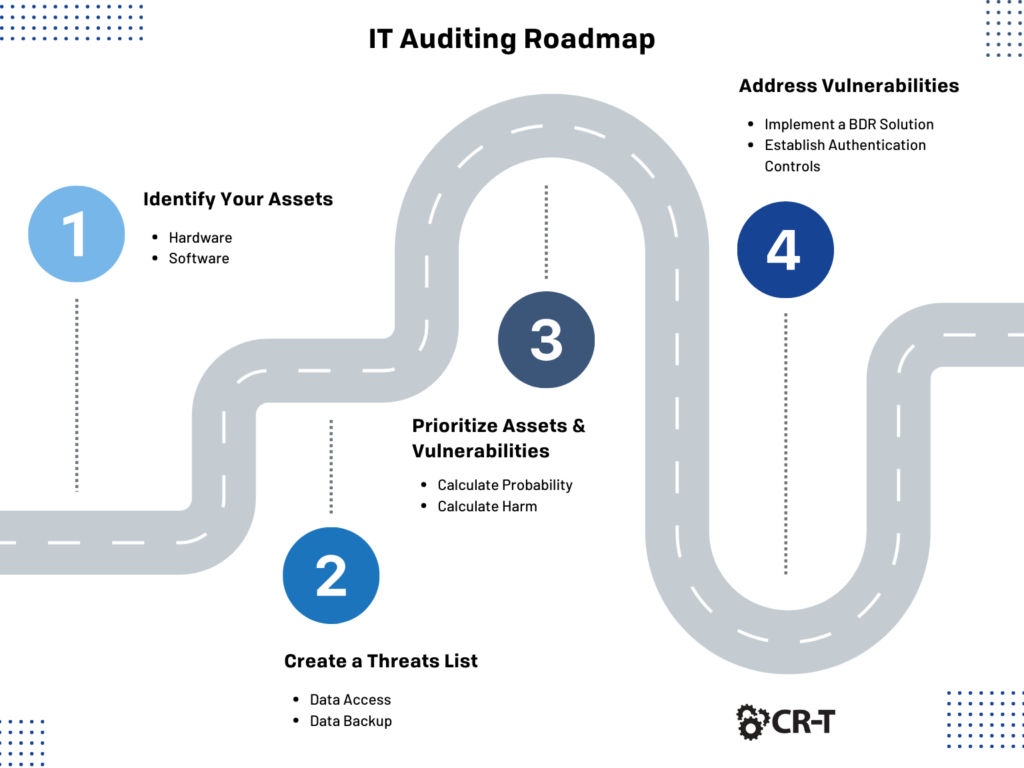
Step 1. Perform Auditing and Mapping.
When’s the last time you’ve performed an audit of your network?
Having a clear understanding of your network’s infrastructure will give you a better idea of where your organization stands when it comes to network security. Auditing and mapping your network will also help you identify any security gaps or vulnerabilities that should be addressed.
Hardware
Begin with your hardware. Identify all the switches, routers, servers, PCs, mobile devices, and wireless access points that exist on your network.
As you comb through your hardware, make a record of the following:
- When was the last time the device was updated or replaced?
- What is the lifespan for the device?
- Does the device display any physical defects?
- Is the device properly labeled with a physical ID tag or similar identification?
- Are the device’s environmental conditions adequate? For example, is the room temperature controlled properly? Is there enough space to house the hardware and perform maintenance on it?
- Which IP address is assigned to the device? Are there any special requirements related to the IP address?
Software
Your software will typically be divided into two main categories. First, there are applications and the Operating Systems (OS) that host them. Second, there may be software-defined networking components, such as VPNs and virtual machines.
As you assess the state of your software resources, make a record of the following:
- Is the resource a standard software resource (application/OS) or a software-defined network infrastructure component?
- When was the last time the resource was updated?
- How much bandwidth does the resource consume? Is there adequate bandwidth available?
- Which IP addresses are used by the resource? How are these IP addresses configured?
- Is there any licensing information available for the resource, and are the license(s) up to date?
Keep Your Network Up to Date
An important facet of performing regular audits is ensuring that each of your network infrastructure components is up to date.
Log into each component to ensure that the default passwords have been changed and examine any other security features or functionalities that haven’t yet been implemented.
Next, analyze each of the devices connected to your network. Ensure that the basics have been taken care of, including operating system and driver updates, activating firewalls, installing antivirus, and resetting any necessary passwords.
Consult an Expert
In addition to performing your own audit, your organization will benefit from an external audit. Meeting with a third-party expert will provide you with a fresh perspective and additional insight into ways you can strengthen your network security.

Step 2. Conduct Regular Risk Assessments.
In addition to auditing and mapping your network, it’s important to conduct regular risk assessments to help you discover potential vulnerabilities that could put your network at risk.
Consider adopting a continuous risk monitoring strategy to make you aware of potential risks as soon as they arise.
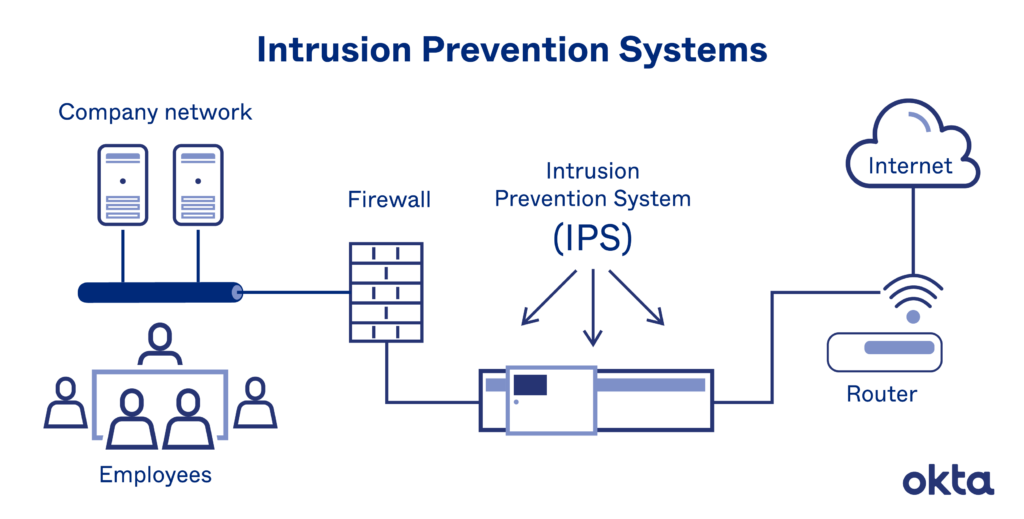
An Intrusion Prevention System (IPS) continuously monitors a network for malicious activity and takes action to prevent vulnerability exploits.
There are several techniques that an IPS will use to identify threats:
- Signature-based detection relies on a dictionary of uniquely identifiable patterns (or signatures) embedded in the code of each exploit. When a new exploit is discovered, its signature is recorded and stored in a continuously growing dictionary of signatures.
- Anomaly-based detection monitors for abnormal behavior by comparing random samples of network activity against a baseline standard. When the sample of network traffic activity falls outside the parameters of baseline performance, the IPS takes action to handle the situation.
- Policy-based detection employs security policies defined by the organization and blocks activity that violates these policies.
Step 3. Develop a Security Strategy for Your Organization.
After completing your risk assessment, you’ll have a more comprehensive understanding of the gaps in your security.
The next step is to develop a security strategy that addresses potential vulnerabilities and ensures data assets are protected.
A Virtual Chief Information Security Officer (vCISO) is a valuable resource that will aid your in-house IT department by offering additional resources and expertise surrounding network security.
Here are just a few areas in which a vCISO can support your organization:
- Security strategy and consulting
- Creating a customized IT roadmap
- Developing security risk management procedures and checklists
- Designing your security framework
- Continuing consulting and education with in-house security teams
Step 4. Understand Network Traffic Patterns.
When analyzing your network’s traffic, ask yourself: Do I understand all the network traffic patterns within my organization? Can I account for both incoming and outgoing network traffic?
After you’ve identified potential vulnerabilities, consider which solutions and policies will best address the risks you’ve encountered.
Here are some ideas to get you started.
Firewall
Firewalls are an integral part of the networking system. A firewall acts as a gatekeeper between your trusted internal system and unverified external networks.
Think of a firewall as the first line of defense. By using an established set of network rules and policies, a firewall monitors and filters incoming traffic, thereby preventing threats from accessing the network.
Antivirus and Anti-Malware Software
Malware, or “malicious software,” is a common type of cyber-attack that takes many forms, including viruses, worms, Trojan attacks, spyware, and ransomware. Some forms of malware immediately steal or corrupt data, while others lie dormant for long periods of time and allow hackers a backdoor into your network.
Antivirus and anti-malware software shields the network from malware by performing regular scans and reporting suspicious behavior. The best forms of antivirus software will monitor network traffic in real time for malware. When a problem is detected, such as data infected with a virus, the software will provide threat remediation to eliminate potential risks.
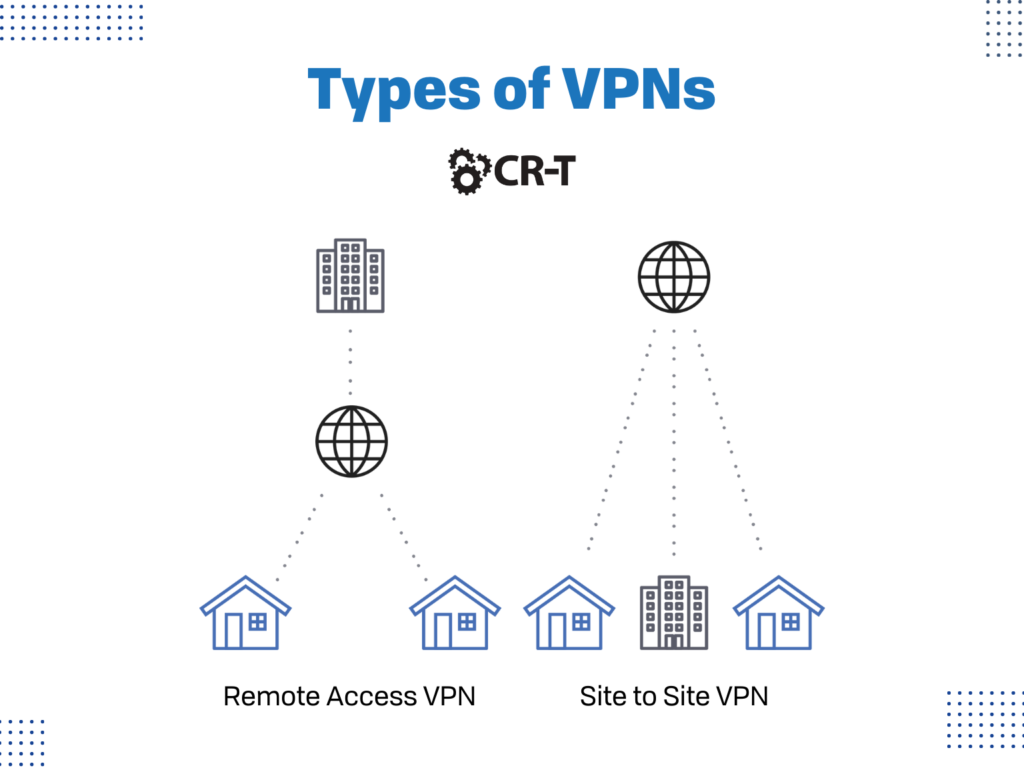
Virtual Private Network (VPN)
If members of your organization access the network from more than one location, consider utilizing a virtual private network.
Virtual Private Networks (VPNs) offer network protection by encrypting the contact between the network and its endpoint, typically over the Internet. Most often, VPNs operate by using Internet Protocol Security (IPsec) or Secure Sockets Layer (SSL) to authenticate communications from devices to secure networks.
There are two types of VPNs: site to site VPNs and remote access VPNs.
Site to site VPNs, also known as router-to-router VPNs, use the IPsec security method to create an encrypted tunnel from the customer network to the remote site of the customer. Multiple users aren’t allowed with site-to-site VPNs.
In contrast, remote access VPNs allow multiple users to connect to the network at the same time. Individual users can connect to the private network, which then allows them to access the services and resources of that network remotely.
Cloud Security
Applications and workloads are no longer hosted exclusively on-premises in a local data center. Many businesses are moving to the cloud to benefit from increased efficiency, reduced costs, integrated tools, and easier collaboration.
However, cloud migration comes with its own set of challenges. When users can connect directly to the Internet, you and your IT department lose visibility into employee activity and increase the risk of data being exposed.
As organizations continue to incorporate cloud-based tools and services, cloud security is a must.
You should always check with your Cloud Service Provider (CSP) to understand which security measures are covered by the provider and which tools you need to implement yourself in order to protect your organization.
Step 5. Understand User Behavior.
In addition to recognizing network traffic patterns, it’s important to understand the habits of your users.
Understanding how users typically behave within a network can help you more easily identify behavioral abnormalities. To start, you and your security support personnel need to establish a baseline of what constitutes normal behavior for specific users, applications, and networks.
Behavioral analytics software is designed to help identify common indicators of abnormal behavior, which can often be a sign that a security breach has occurred. This allows you to more quickly spot problems and isolate potential threats.
Catching an anomaly early can save you a huge headache and thousands of dollars in the long run.
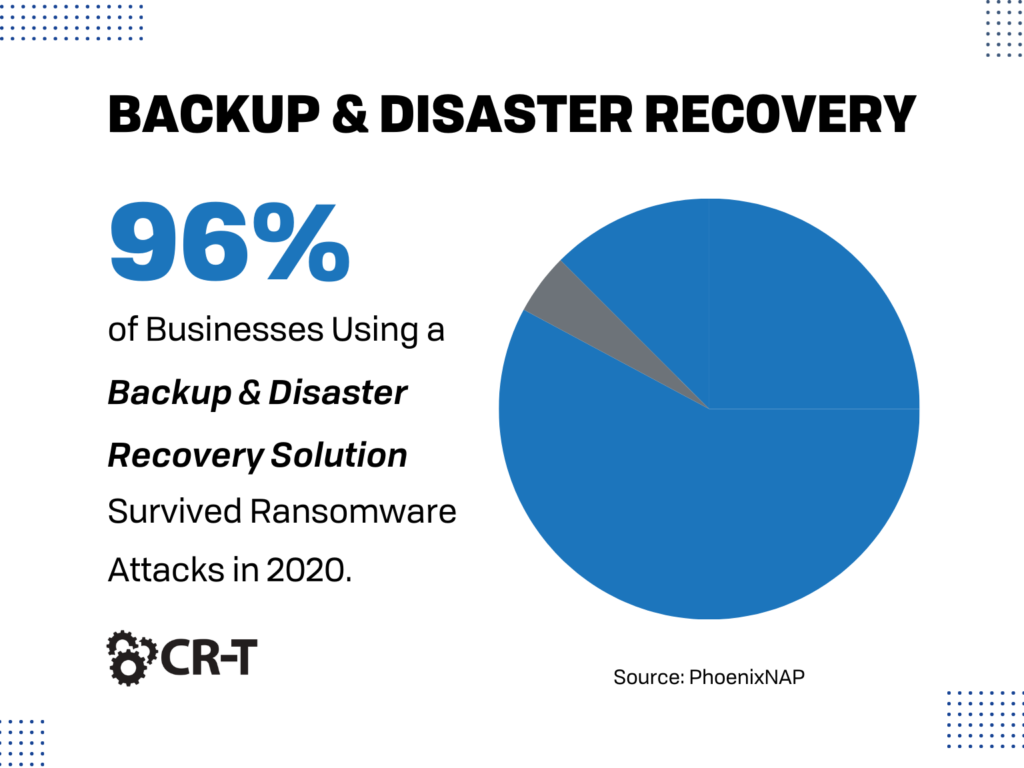
Step 6. Implement Backup and Disaster Recovery (BDR).
Data loss is practically inevitable, but it doesn’t have to cripple your organization.
By implementing a Backup and Disaster Recovery (BDR) solution, you can ensure that your data remains protected and accessible in case of a security breach.
BDR relies on a two-pronged approach:
- Data backup is the process of replicating files to be stored at a designated, secondary location.
- Disaster recovery is a system that allows you to quickly restore your data in the event of a system failure.
BDR is one of the most critical tools you have in your security arsenal. Investing in BDR ensures that your data remains protected, and that downtime is minimized in case of a security breach.
Step 7. Establish Strong Authentication Controls.
One of the most effective ways to prevent a security breach is through implementing strong authentication controls.
Multi-factor authentication and network access control are two of the most effective ways to protect your network from malicious intruders, while also ensuring that users only have access to the necessary data, they need to perform their jobs.
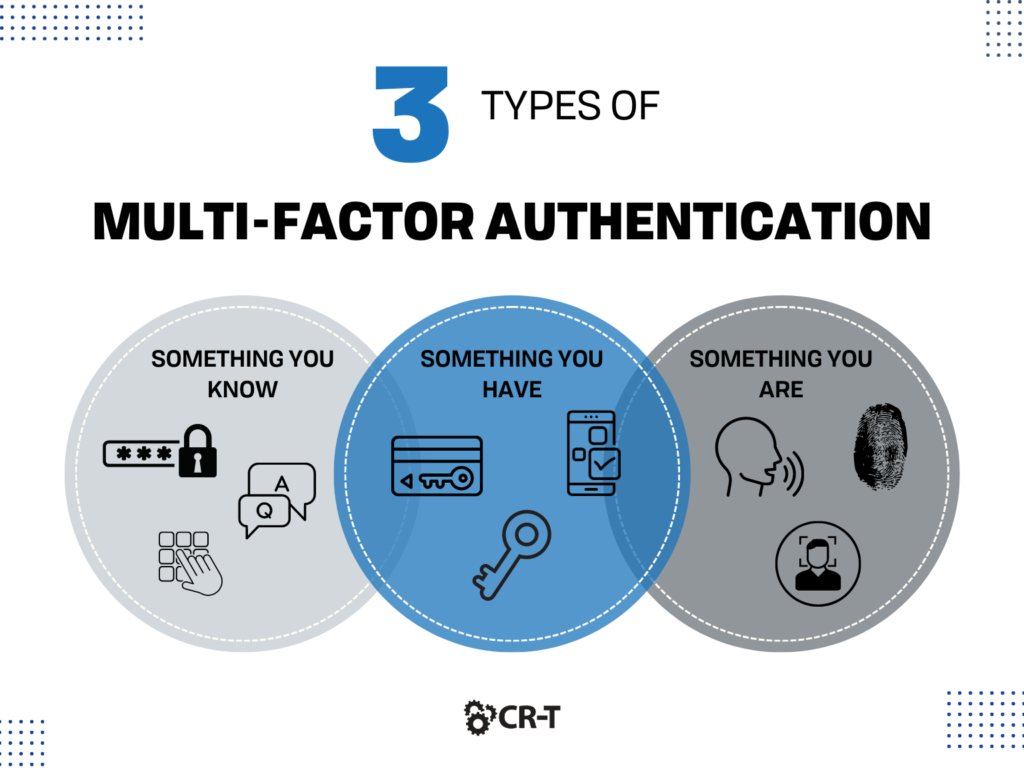
Multi-Factor Authentication (MFA)
Passwords are the norm when it comes to account security. Unfortunately, it can be difficult to remember dozens of unique, complicated passwords. And storing them securely is a whole other issue.
Instead of relying solely on passwords, consider adopting a more secure alternative.
Multi-Factor Authentication (MFA) requires users to provide two or more forms of authentication when logging into an account.
If a hacker steals your password but you have multi-factor authentication enabled, it’s suddenly much more difficult for a hacker to get into your account. This is especially true if one or more of your authentication methods utilizes something unique to you as an individual, such as a fingerprint, face recognition software, or a verification app on your phone.
Overall, multi-factor authentication is much more reliable and secure than simply using a password. MFA is a tool that every organization should carry in their arsenal.
Network Access Control (NAC)
Your organization’s network might have a lot of visitors, but not all of them should have the same level of access.
Network Access Control (NAC) limits who can access the network, and more specifically, who has access to sensitive data within the network.
Network access control utilizes a variety of authentication methods to identify its users and deny unsanctioned access.
In addition to network access control, there are multiple access-based security measures available, depending on the needs and size of your organization. These measures include the following:
- Identity Access Management (IAM)
- Attribute-Based Access Control (ABAC)
- Role-Based Access Control (RBAC)
- Zero Trust Network Access (ZTNA)
By limiting who can view and download sensitive information, these security measures keep your data protected and reduce the risk of a security breach.
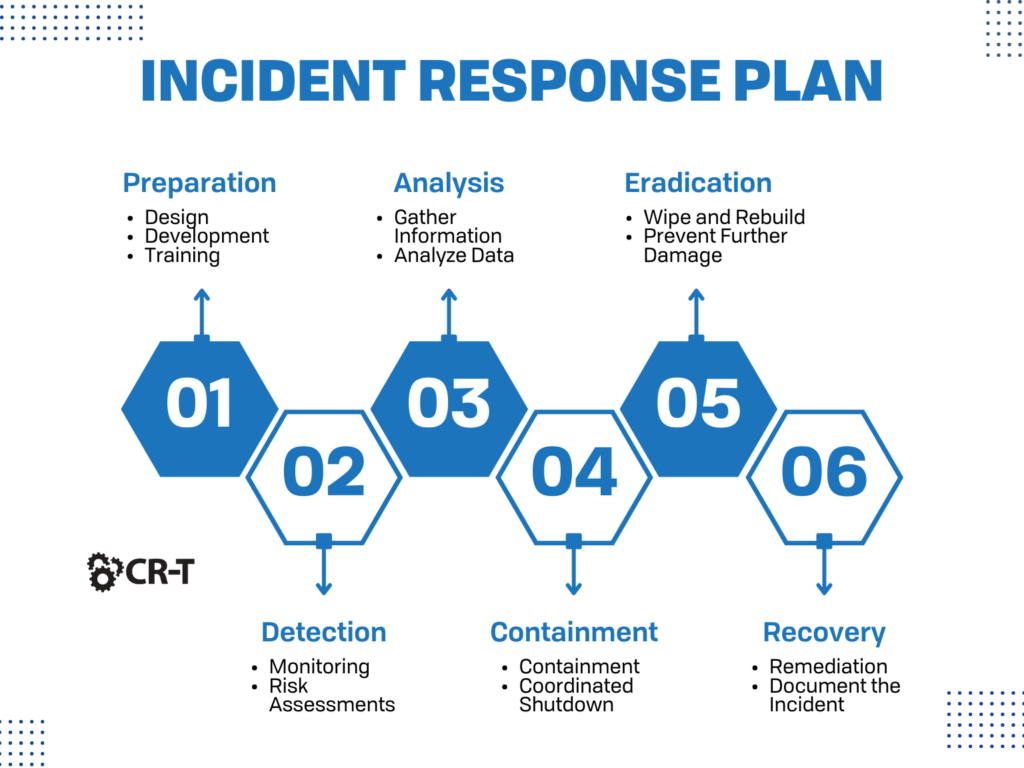
Step 8. Develop an Incident Response Plan.
Despite your best efforts, no organization is completely immune to a cyber-attack.
Having strong security measures in place will certainly help, but it’s also important for you to have a plan for how you will respond if you fall prey to a security breach.
By now, you’ve hopefully identified all possible threats and vulnerabilities. Now it’s time to create a specific dialogue about what will happen in the case of a cyber-attack. Who is responsible for isolating the attack? Who will notify your affected clients about the breach? How will you know when the consequences of the attack have been resolved?
Every member of your organization should understand their roles and responsibilities following a cyber-attack.
Make sure your incident response plan is regularly updated and that your employees know exactly what to do in case of a security breach.
Step 9. Train Your Users.
Your users are your best line of defense when it comes to preventing a security breach.
Train your users on cybersecurity best practices, and review policies on how to manage data. Perform routine experimental phishing campaigns to determine how well users can identify suspicious emails.
Make sure users are aware of non-technical methods used by hackers—such as social engineering tactics—to extract information about your organization.
Step 10. Invest in Cyber Insurance.
Are you still worried about the potential losses of a cyber attack? Cyber insurance is yet another option that can help protect your business.
Every insurance policy is different but investing in cyber insurance now can save you money in the future and cover your organization’s liability for a data breach involving sensitive customer information.
Discuss with your insurance agent which policy would best fit your company’s needs.
FAQs About Strengthening Network Security
Q: What are the first steps I should take to strengthen my network security?
A: First, create an inventory of your organization’s assets. This includes anything attackers might want to take control of, like devices, servers, and data. Next, perform a risk assessment to identify potential threats and determine their impact on your organization. From there, you can meet with a vCISO and develop a security strategy that addresses any potential threats.
Q: How can I secure my network traffic?
A: Firewalls, antivirus software, and VPNs are all great options for securing your network traffic.
Q: How do I establish authentication controls?
A: Both multi-factor authentication and network access control will strengthen your accounts’ security and enable you to choose who can access which information within the network.
Conclusion
Cybersecurity doesn’t have to be complicated.
After following our tips and best practices for success, you’ll be well on your way to establishing strong network security for your organization.
You can start right now by performing an audit of your network.
As you continue to address potential threats and fill in any gaps, you’ll be laying a strong security foundation that will provide peace of mind and greater success for all the members of your organization.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of

