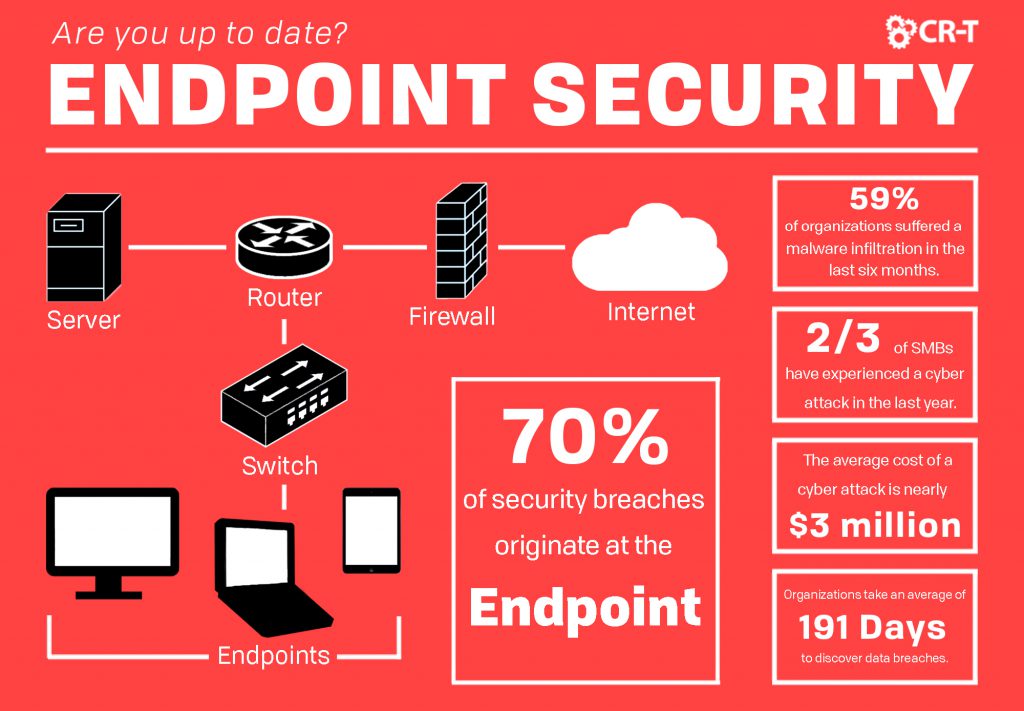
As security threats continue to evolve, it’s becoming more important than ever to keep your security up-to-date. According to Absolute, 70% of security breaches originate at the endpoint, meaning that your company could be at risk, even if you already use antivirus protection. Having the latest in endpoint technology will help you keep your network secure, while still allowing for data sharing and the use of offsite devices. This article will outline the ways endpoint security can benefit your company and explain why it’s essential for you to keep your security solutions up to date.
While antivirus was once enough to protect an entire network, sophisticated threats have made it so this is no longer possible. According to a 2018 Ponemon report, two-thirds of SMBs have experienced a cyber attack in the past year. And the average cost of an enterprise-level attack is nearly $3 million. Endpoint security is your first line of defense against attacks, and you can ensure a safer network by keeping your security measures up-to-date.
What is Endpoint Security?
Endpoint security programs or solutions are used to secure various endpoints on a network. Each endpoint represents a point in a communication channel, such as a server or mobile device.
With various devices located throughout the network, endpoint security is a must. Locking down endpoints and only allowing specific traffic to enter the network makes it more difficult for malware and other security threats to pass through.
For enterprises, endpoint security also offers centralized management, making it a great option for businesses who want control over their security, without forfeiting the quality.
Unlike antivirus, which secures individuals devices, endpoint security protects the entire network, filtering traffic that comes through the endpoints, while also monitoring and logging activity to safeguard those endpoints.
Endpoint security usually consists of software that authenticates logins made from the endpoints. By using just one system for all of your security needs, you can minimize complexity and experience greater control.
Why is Endpoint Security Important?
Policies like Bring Your Own Device (BYOD) are becoming more popular, but they also decrease your overall security perimeters. Standard cybersecurity systems have loopholes that hackers are quickly learning how to exploit. On top of this, business owners often leave endpoint security to their employees, expecting them to follow security procedures and regularly perform updates.
Being complacent with your security procedures creates gaps in the infrastructure, creating problems for you in the future. Don’t leave your security to chance. You can ensure that your network is protected by taking the necessary steps to secure every device and network entry point.
With endpoint security, you can avoid excess server downtime. According to Gartner, a downtime outage can cost an average of anywhere between $140k and $540k per hour.
Endpoint security also allows you to track user behavior so you can gain greater control of your data. With a fast and easy deployment of new security technologies, hardware and software compatibility, and broader threat protection, endpoint security is an investment that will save you time and money in the long run.

How Can Endpoint Security Help You Stay Protected?
Data Loss Prevention
An important aspect of endpoint security is data loss prevention (DLP). Endpoints often hold sensitive information, and with the high amount of traffic they experience, it’s becoming easier for outside users to enter the network and compromise its security.
Endpoint security offers a variety of DLP options that monitor and protect your network’s information in order to prevent data loss. DLP classifies sensitive data and regulates policy violations, allowing for real-time monitoring and detection.
With content discovery, you can also enable automatic scanning to help you detect policy violations more quickly. Endpoint DLP supports network policies for offsite devices, so you don’t have to worry about compromised security on company laptops and mobile devices.
Insider Threat Protection
Another major benefit of endpoint security is insider threat protection. With endpoint security, you can easily gain visibility into potential insider threats, allowing you to identify and mitigate malicious internal threats before they can damage your network.
Endpoint security allows you to prove or disprove malicious user intent, helping you anticipate potential risks, such as data theft. You can also monitor employee communication channels, allowing you to better protect employees from harassment.
Disk, endpoint, and email encryption all help you prevent unauthorized access by only sharing information with approved individuals. Encryption works by coding information and requiring credentials in order to access the data, helping you strengthen data security by blocking unauthorized access.
Key sharing allows users to share files securely, while providing multiple layers of protection, through both drive encryption and file encryption. Encryption also supports compliance requirements, while keeping you updated on policies and enforcements. With endpoint encryption, you can protect removable media, local data, and cloud data from intruders.
Endpoint Detection and Response
When it comes to security breaches, critical systems are the most targeted, since they usually contain the most sensitive information. Trustwave estimates that 59% of organizations have suffered from a malware infiltration in the last six months.
Application whitelisting helps you prevent malware infections by only permitting trusted software to run. This allows you to lock endpoints and only grant access to the applications you authorize. Administrators can also manually view and block malicious applications.
According to CSO, organizations take an average of 191 days to discover data breaches. And 77% of attacks in 2017 were fileless. Endpoint detection and response (EDR) allows you to detect and investigate suspicious endpoint activities by recording, storing, and analyzing information.
EDR creates a comprehensive data analysis that helps you more easily identify suspicious activity. With continuous surveillance and a real-time response to threats, EDR is a great tool to add to your endpoint security infrastructure.
Endpoint security isn’t just about protecting your data, however. With data classification, you can also organize your data to make it easily searchable and trackable. Classifying data helps you quickly identify sensitive information in order to prevent security gaps. Data classification can also help you maintain compliance by ensuring that all of your data follows government and industry regulations.

Are You Up-to-Date on Your Endpoint Security?
While you may feel confident about your current level of security, it’s important for you to stay updated on the latest security options. Panda Security revealed that 230,000 new cases of malware appear daily—and the number is only growing. Companies are still at risk, and unless your endpoint security is up to date, regular security measures might not be enough.
There are several things experts recommend that every company should be doing to secure their endpoints. First, use multi-factor authentication on all endpoints. Additionally, employees should receive regular end-user security training. A number of trends have emerged in recent years that you can implement to strengthen your network through endpoint security.
Cloud and Artificial Intelligence Technologies
Migrating to the cloud is becoming more popular every year, and cloud security can help to strengthen your existing infrastructure. Cloud-based endpoint security offers additional security options, like antivirus validation and the ability to identify specific types of advanced malware.
Utilizing the cloud can also save you money, while giving you additional storage. Cloud security requires less maintenance than other cybersecurity options. For businesses that are already transitioning to the cloud, hosting your endpoint security in the cloud is a no-brainer.
With the development of new technology and the evolution of advanced threats, artificial intelligence (AI) has become invaluable, using machine learning to distinguish threats more quickly and lead companies to security automation.
According to E-Security Planet, 79% of organizations are utilizing automation as part of their security approach, including AI. This technology has proved increasingly effective against sophisticated threats.
Through machine learning, AI algorithms use statistical techniques to analyze data and detect threats. These threats can then be stopped at the endpoint level, before they cause any lasting damage.
Endpoint Protection Platforms
Utilizing a variety of security measures can make a network more difficult to organize and maintain. Consolidate endpoint security tools into a single agent that can help you monitor endpoint activity and take appropriate action.
Additionally, both EPP and EDR are affecting the evolution of endpoint security. An endpoint protection platform (EPP) is simply a security program designed to protect endpoints, while an endpoint detection response (EDR) will detect and investigate security threats in order to make them easier to eliminate.
By consolidating both EPP and EDR into a single endpoint security solution, you can enjoy all the benefits that EDR has to offer, while also relying on the added protection of EPP.
As cybercrime continues to evolve, past security solutions are becoming insufficient to handle the attacks. Next generation endpoint offers the security you need to move past security threats. Supplement your antivirus and firewall protection with a holistic security approach that includes endpoint security.
We can help you find an endpoint security solution that will prepare you against future threats.
Start Today—Get a Free Consultation
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of





